Understanding the Basics of Security Testing in Software Testing
In This article
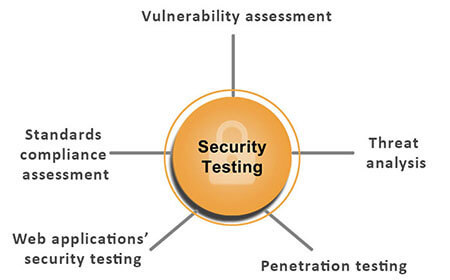
Security testing is an important aspect of software testing that helps to identify and resolve security threats before they become problems for you and your users. In this article, we’ll discuss the basics of security testing in software testing, including what it is and why it is important. We also explore the types of security testing and best practices for implementation.
What is Security Testing and Why is it Important?
Security testing in software testing is the process of evaluating your software to identify vulnerabilities or weaknesses that could be exploited by hackers or attackers. The importance of security testing cannot be overstated, as it helps to ensure that software is secure and can protect sensitive data and information from unauthorized access or misuse.
One crucial benefit of security testing is that it protects against cyber-attacks which are becoming increasingly sophisticated. Security testing can help identify potential security threats in your software, allowing you to take steps to address them before they cause major problems.
Also, security testing helps you stay compliant with regulations. Depending on your industry and region, there may be specific regulations and standards that your software must meet. Security testing can help ensure that the software meets these requirements, avoiding potential penalties or legal issues.
Additionally, users want to know that their data is secure when using your software. So, while you focus on creating a SaaS marketing plan, you also want to put structures in place for conducting security testing and addressing vulnerabilities. This way, you can enhance user confidence in your software and build trust with your customers.
Types of Security Testing
Now, let’s explore the various types of security testing in software testing. An efficient combination of these testing methods will ensure that your software is secure and protected against cyber attacks.
Vulnerability Scanning
Vulnerability scanning is the process of scanning software for known vulnerabilities or weaknesses. This type of testing involves using automated testing tools to identify potential security flaws in your software. Examples of such flaws include outdated software components, weak passwords, or insecure network configurations.
Vulnerability scanning can help identify security weaknesses that may be present in your software before they can be exploited by attackers.
Penetration Testing
Penetration testing, also known as “pen testing,” involves simulating a real-world attack on your software to identify vulnerabilities and weaknesses. This type of testing typically involves ethical hackers or security professionals attempting to exploit security weaknesses in your software.

Penetration testers look out for vulnerabilities associated with authentication and authorization flaws. It also looks out for security weaknesses related to network configurations, such as open ports or unencrypted network traffic.
Penetration testing can also assess application logic flaws—these are vulnerabilities related to the way your software processes user input or executes specific actions.
Risk Assessment
Risk assessment involves identifying potential threats to your software and assessing the likelihood and negative impacts of those threats. This type of testing typically involves analyzing the software’s architecture, design, and implementation to identify potential security risks — for example, data breaches, denial of service (DOS) attacks, or malware and viruses.
The risk assessment will also provide recommendations for improving your software’s security based on the risks identified. This way, you can take proactive measures to address these issues.
Ethical Hacking
Ethical hacking is similar to penetration testing in that it involves simulating real-world attacks on your software. Ethical hacking can help identify vulnerabilities that may be missed by other types of security testing. Some of these vulnerabilities include phishing attacks, social engineering attacks, or physical security breaches.
Ethical hacking can provide a more comprehensive assessment of your software’s security by testing a broader range of attack scenarios.
Security Scanning
Security scanning involves using automated tools to scan software for potential security vulnerabilities. These tools may include software or hardware-based scanners that can detect a wide range of security issues.
Security scanning may include tests for common vulnerabilities such as SQL injection, cross-site scripting (XSS), and buffer overflow attacks.
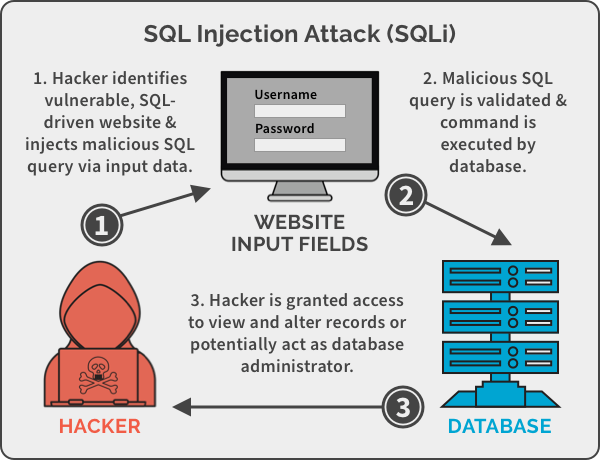
Security scanning can also help you comply with industry standards and regulations related to software security. While security scanning can be a valuable tool in identifying potential security weaknesses, it should not be the only type of security testing that you rely on. This is because security scanning tools may not catch all software vulnerabilities. It may also produce false positives or negatives.
Therefore, it’s important to combine security scanning with other types of security testing such as penetration testing and risk assessment. With this, you’ll have a more comprehensive assessment of your software’s security.
Posture Assessment
Posture assessment involves analyzing the overall security posture of your software. This type of testing typically involves reviewing the software’s security policies and procedures to identify loopholes.
During posture assessment, security experts may review your access controls and software endpoints to help you prevent malicious attacks that may be targeted at your software.
The assessment highlights the need for strategic improvements in operational and tactical improvements. It’ll also help to ensure that your organization’s security posture is not weakened by its service providers or other third parties.
Additionally, posture assessment can involve reviewing your software’s incident response plan to ensure that you have appropriate procedures in place to respond to security incidents. This may include testing your ability to detect and respond to security incidents, as well as testing your ability to recover from a security breach.
Security Auditing
Security auditing involves a comprehensive evaluation of the software’s design, implementation, and operational processes to identify gaps in your security controls. When running security audits, start by defining a scope and objective that outlines the purpose, goals, and expected outcomes of your audit.
Next, gather relevant information about the software’s architecture, design, and implementation to identify potential areas of weakness. You can do this by reviewing the software’s documentation and interviewing key stakeholders alongside running vulnerability scans and penetration testing.
During the auditing process, identify and prioritize potential security weaknesses, vulnerabilities, and gaps in security controls. Then, develop recommendations for resolving the threats and improving your security controls based on the audit results.
7 Best Practices for Conducting Software Security Testing
A well-implemented security testing helps you detect and remediate vulnerabilities early in your software development lifecycle. This reduces the likelihood of costly security breaches and data loss when you eventually get new users through your 10X content marketing strategies or social media promotions.
To achieve precise and accurate security testing in software testing, you should follow best practices that ensure the process is comprehensive, efficient, and effective. The best practices we discuss below can help you achieve this:
1. Identify the Security Requirements
Before conducting security testing, it is important to identify the security requirements for the software. This will help to ensure that the testing is focused on the most important security issues.
To identify security requirements, start by reviewing relevant security policies and regulatory standards that apply to your software. These can include industry-specific regulations, such as HIPAA or PCI DSS, as well as general security standards, such as ISO 27001 or NIST SP 800-53.
Next, assess the software’s risk profile and determine the potential impact and likelihood of different types of security threats and attacks. This can involve conducting a threat modeling exercise or a risk assessment to identify and prioritize security risks.
Finally, specify security requirements based on the identified risks and applicable regulations and standards. These requirements should be clear, measurable, and testable. They should also cover different aspects of security, such as confidentiality, integrity, availability, and non-repudiation.
2. Design Security Tests
Based on the security requirements, design security tests that will identify previously unknown vulnerabilities and weaknesses. To design security tests, you need to identify the different types of security tests that are relevant to your software — we already discussed the different types of security tests. Then, define the scope and objectives of each test.
Develop test cases and scenarios that simulate real-world attacks. Consider the potential impact and likelihood of each vulnerability, and prioritize testing efforts based on risk assessment.
Finally, document the test plan and share it with stakeholders for feedback and approval. Make revisions to the plan based on the feedback you receive and get ready to execute.
3. Execute Security Tests
When executing security tests, make sure to follow the designed plan carefully to ensure that you accurately perform all the tests. Take note of any issues that arise during testing and document them for later analysis. Use a systematic approach to ensure that all tests are completed, and no vulnerabilities are missed.
To facilitate the workflow during security testing, consider using security testing tools that automate the testing process and provide detailed reports on vulnerabilities and weaknesses. This can save time and ensure that all tests are performed consistently.
Additionally, make sure to involve your development teams and security experts in the testing process to ensure that all potential issues are addressed.
4. Analyze the Results
Analyzing the results of security tests is a critical part of the software security testing process. It involves examining the data collected during testing to identify potential security issues that need to be addressed.
To effectively analyze the results of security tests, ensure that the testing results are documented thoroughly and accurately. This documentation should include details on the tests that were performed, the results obtained, and any issues or vulnerabilities identified during testing. This information will be crucial in determining the severity and priority of each issue and in developing a plan for addressing them.
It’s also important to seek feedback from professionals as their expertise and insights can help develop effective strategies for addressing the vulnerabilities.
5. Fix the Vulnerabilities
Once potential vulnerabilities have been identified, take steps to fix them to ensure that the software is secure. When fixing vulnerabilities, it is important to prioritize them based on their severity and potential impact on the software’s security.
Critical vulnerabilities should be addressed first, followed by those with medium and low severity. It is important to develop a plan for remediation that addresses all identified vulnerabilities and includes a timeline for completion.
You should also use secure coding practices when fixing vulnerabilities, such as input validation and output sanitization, to prevent similar vulnerabilities from occurring in the future.
6. Retest the Software
After the vulnerabilities have been fixed, retest the software to ensure that the fixes were effective. This is crucial as fixing one vulnerability may create another one if not properly tested.
When retesting the software, make sure to follow the testing plan and procedures that were established in the previous testing phase. Also, use the same testing tool if possible to maintain consistency. It is also important to note that retesting should not only be done after software fixes but also after any changes or updates have been made to the software.
7. Report the Results
Report the results of the security testing to stakeholders to ensure that everyone is aware of any potential security issues and the steps taken to address them.
To make security testing reports effective, use clear and concise language that avoids technical jargon. Using an effective AI content generator can help you create a report that’s easy for all stakeholders to understand. Including a summary of findings is also crucial in providing an overview of the testing process, key findings, and recommendations for remediation. This summary can be used as a starting point for further discussion and decision-making.
It’s also advisable to use supporting evidence such as screenshots, log files, and vulnerability reports can be used to support the findings in the report. This evidence adds credibility to the report and helps stakeholders understand the severity of the vulnerabilities.
Finally, provide actionable recommendations which stakeholders can implement as a part of their security measures.
In Closing
Software security testing is crucial for identifying and addressing potential vulnerabilities and weaknesses that could compromise the security of the software. We discussed several types of security testing, including:
- Vulnerability Scanning
- Penetration Testing
- Risk Assessment
- Ethical Hacking
- Security Scanning
- Posture Assessment
- Security Auditing
To conduct precise and accurate security testing, it is important to follow best practices such as identifying security requirements, designing security tests, and executing the tests systematically. You should also analyze the results, fix vulnerabilities, retest the software, and report the results effectively.
By implementing these best practices, you can ensure that your software has the perfect security against potential threats from hackers.